It turned out that ChatGPT can easily create a phishing email that anyone will believe, or write a malicious program that will find and extract sensitive data from a computer or spread viruses.
What’s next? Artificial intelligence for us friend or foe? Is it a dangerous toy in the hands of criminals? Let’s take a look at what GPT chat can really do, how much stronger it has made cyber criminals, and how to best defend yourself in today’s cyber world.
Plan of the article:
- Portrait of a cybercriminal in the era of ChatGPT
- Exactly how scammers use GPT chat
- How to recognize fraudulent attacks
- YubiKey’s hardware devices against phishing
Portrait of a cybercriminal in the era of ChatGPT
Experts of the site LexinForm note that cybercriminals fall into a fairly wide range of people: from highly qualified specialists to ordinary amateurs. All of them have different status in society, different professional knowledge, occupy different positions: from a storekeeper to a boss. Hackers and crackers also differ in their level of education. But still, thanks to the research of domestic and international experts, it was possible to create a typical portrait of a computer criminal.
The future criminal gets acquainted with the computer since childhood. Adores and explores it by all available means. He tries to acquire the necessary skills for working with a computer both in lectures on informatics, cybernetics, neurobionics, and on his own, studying computers, information technologies, and various communication networks, such as the Internet and its analogues.
The age of offenders ranges from 15 to 45 years, of which:
| 33% | up to 20 years |
| 54% | from 20 to 40 years |
| 13% | older than 40 years |
About 83% of fraudsters in the world are men. If they are women, they have the following professions: secretary, accountant, economist, controller, etc. It should be noted that the female share in this area is constantly growing, as women begin to master technologies and become interested in “male” professions, such as programming.
It is interesting that a significant proportion of hackers or crackers have weak language skills and write with mistakes. But at the same time, their IQ is above average. Although in general, according to this parameter, cybercriminals are divided as follows:
| 21% | IQ above average |
| 77% | average IQ |
| 2% | IQ below average |
This is because not all cybercriminals are hackers. In general, criminals who engage in hacking are more often called crackers. There are about 180 crackers for one hacker. Because hackers are high-class specialists who have an unusual worldview and certain beliefs. Some of them may even cooperate with the law, helping to catch criminals. These are the so-called “white hackers”.
In addition to hackers and crackers, there are attackers who specialize more in social engineering. We talked about this direction in more detail in the article: “How to protect yourself and colleagues from convincing “specialists” in social engineering”.
Interestingly, nowadays, attackers do not have to have great mathematical abilities and programming skills. Also, now they will be able to write without mistakes. Because the GPT chat writes without typographical errors, but may allow syntactical errors (which most people who do not have a professional education as a philological editor usually do not notice).
So the intelligence distribution among attackers can now change: many of those with an average IQ will be able to hack or write malware; and those with a lower than average IQ will be able to deceive people very successfully by creating and sending them very effective and persuasive letters.
Next, we will give several real examples of the use of artificial intelligence by criminals.
Exactly how scammers use GPT chat
Creating an information stealer
Наприкінці 2022 року на одному з популярних хакерських форумів з’явилася тема «ChatGPT – Переваги шкідливих програм». У ній підкреслено переваги шкідливого програмного забезпечення, яке було створено автором за допомогою штучного інтелекту. Серед іншого він поділився кодом, який створив чат GPT на Python. Цей код може знаходити файли багатьох типів, наприклад .txt, .docx, .pdf, .jpg тощо, копіювати їх у випадкову папку Temp, архівувати та завантажувати на віддалений сервер.
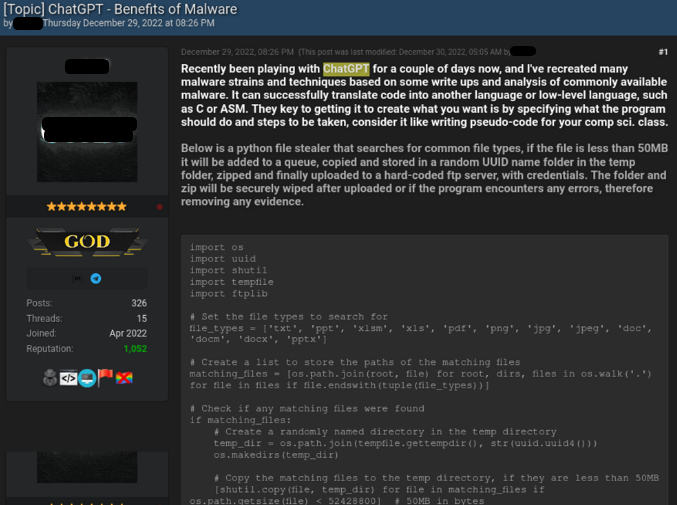
In this way, files from personal computers can get to third parties.
Illegal data encryption
In December 2022, another hacker forum author published a script he created for the first time using GPT chat (also in Python).
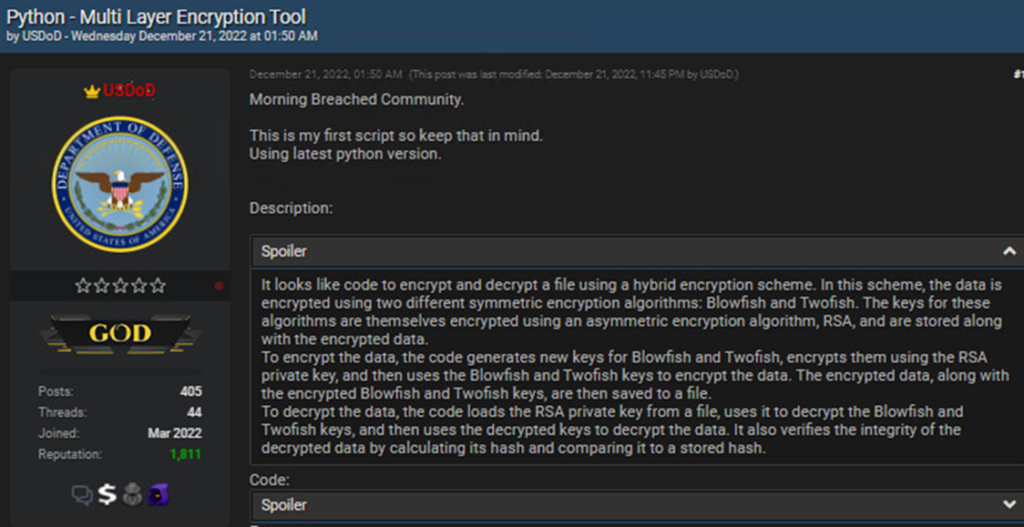
This script is able to implement the following functions:
- Generate a cryptographic key for signing files.
- Encrypt all files in a specific directory.
- Use RSA keys or certificates stored in PEM format, as well as MAC signature and blake2 hash function.
It all looks innocent at first glance, but the script can easily be rewritten to completely encrypt someone’s personal device. That is, this script can easily be turned into a ransomware program.
We remind you once again – the code was created by a person without programming skills!
Creation of fake content
As early as the beginning of 2023, many questions were raised on closed fraud forums about the creation of works of art and their subsequent sale on platforms such as Etsy, although with the help of a slightly different tool – OpenAI (DALLE2). By the way, in addition to images, attackers tried to sell e-books created using GPT chat.

Using ChatGPT for phishing
GPT chat easily and quickly generates messages as if from an official service, for example, from a bank employee, a law enforcement officer, from the administration of the postal service or a support manager at a cryptocurrency service. Such a message can appear so convincing that users are forced to download software that then steals information, or to follow a link and fill out a form “to confirm personal data”.
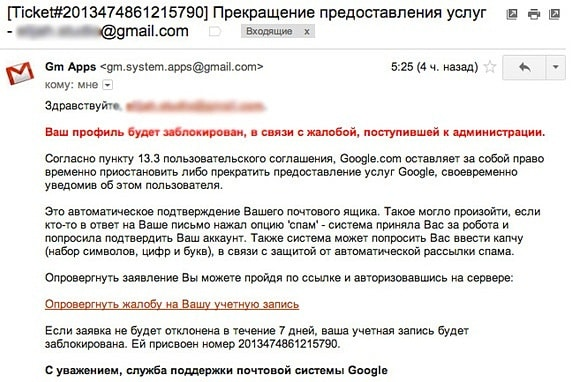
How to recognize fraudulent attacks
If earlier one of the main signs of fraudulent emails was many typographical and other errors, now this parameter can be ignored – with the help of GPT chat, attackers can now write almost perfectly in any language.
So you will have to be vigilant in cases that we will talk about in detail later.
Link
If the link was sent by someone you don’t know, then even if he called himself your employee or your new boss, you should not rush to click on the link and even more so to download any files. Through it, you can download a malicious program: Trojan, spyware, virus, etc.
What to do if you received a link like this:
- Try to find out if the message is really coming from the person it claims to be.
- Check whether other employees received similar offers, how they reacted to them, what happened after that.
- Do not respond to an email if it looks suspicious.
Filling out forms
In addition to malicious files, links can lead to phishing sites with an offer to fill out a form under various pretexts: or to confirm account data or payment information, for example, under the pretext of avoiding blocking.
What to do in this case:
- Remember that no service asks for sensitive information such as account accesses, permanent or one-time passwords or PINs.
- Check who the email is from, whether there are any errors or extra characters in the site’s domain.
- Go to the official site by typing the address manually or through bookmarks if you have saved them before. Log in and check if the account has the quality of a warning or a message from the site administration.
- Do not fill out forms on suspicious sites.
Actual context
Fraudsters quite often use information about current events in communication to add credibility to their messages. Criminals also try to create a sense of urgency to perform some actions. Otherwise, the chance will disappear, or you will get blocked, or the lives of your loved ones will hang in the balance.
How to distinguish fraudulent messages?
We recommend in all cases to be alert if you receive any unusual messages. Of course, a person can still believe scammers if they fall into the right context: you took part in a promotion, and now you receive a message about a win; you just talked to your boss about a promotion or a bonus, and the accounting department allegedly asks to confirm your payment information; you wanted to talk to a relative, but he didn’t answer three times… Fraudsters can also use the national motto “Everything will be Ukraine”, which nevertheless makes a positive impression on a person.
So, to protect your data in any case, we recommend using hardware security keys, which are currently the most effective anti-phishing tool.
YubiKey’s hardware devices against phishing
No matter how smart the criminals are, and no matter what the latest tools are used for this, today they will not be able to bypass the simple and effective protection of accounts using the YubiKey produced by the Swedish-American company Yubico. Because these hardware devices work according to the principle of a key to a house, car, or apartment — only if you have a key can you get inside. Since the key is always with the owner, only he can access his account.
So what happens if attackers steal your password, PIN, or two-factor authentication code? Nothing, because to confirm the login or payment operation, you still need to insert the key into the device and touch the metal part, confirming your presence.
Why exactly YubiKey:
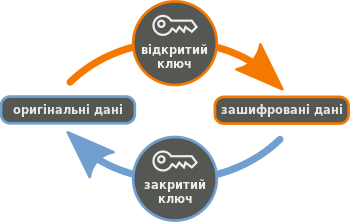
- The keys work on the basis of asymmetric cryptographic encryption, in which one key is for encryption, it is public, and the other is for decryption.
- All YubiKey security keys sold in our online store, have support for FIDO2 protocols — that is, an open driverless protocol for two-factor authentication. That is, the keys work simply “out of the box”.
- Most security keys (you can compare them here) support one-time OTP passwords and smart card functions. They can be configured using YubiKey Manager.
- Global companies such as Google, Amazon, Twitter, Microsoft, Meta use YubiKey security keys to protect their employees’ accounts. By the way, this practice is also implemented in Ukraine, for example, in the companies Naftogaz, Cyber Police, Kyiv Electric Networks, EPAM, FUIB Bank and others.
Do you want to choose reliable hardware devices to protect your accounts or the accounts of your employees? We, as the official distributor of Yubico, invite you to our Internet-shop!
Similar materials on the blog
Cybersecurity outsourcing – is it really dangerous and expensive?
Cybersecurity is a constant race against the clock: hackers find vulnerable chains and try to gain access to confidential information, while security experts build security systems that attackers try to break into after a while. And this happens all the time....
What businesses need to know about information security – an overview of technical tools
Unauthorised access to personal information, financial accounts or trade secrets can cause a lot of damage. This can lead to large losses due to the loss of reputation and financial assets, violation of user privacy, etc. Therefore, every person, organisation, business or financial institution must take care of data protection.
How the YubiKey protects against brute-force attacks: technicalities of attacks and key encryption
How the YubiKey protects against brute-force attacks: technicalities of attacks and key encryptionBrute force attacks are one of the most common hacking methods. It is considered one of the simplest, because in fact, in order to start an attack, an attacker only needs...




