Unlike a static password, a one-time password provides greater security — if an attacker even intercepts it, he may not have time to use it. OTP-passwords are created thanks to the algorithm of random numbers, so the fraudster will not be able to guess which sequence will occur next time. And this is also an advantage of OTP passwords.
Of course, the longer the password, on the one hand, it is more difficult for an attacker to pick it up, but also, on the other hand, it is more difficult for an ordinary user to remember and enter the password manually in time. So in this matter, technology comes to the aid of a person. The YubiKey is one of the most effective, so let’s take a look at how it works.
How OTP passwords work with YubiKey
YubiKey 5 and YubiKey FIPS security key series support several OTP protocols, these are:
Yubico OTP — 128-bit password consisting of 44 characters; 12 of them are immutable, they serve as an identifier for the YubiKey device itself. Such a password is almost impossible to forge. Below is an example of such a password, called three times.
cccjgjgkhcbbirdrfdnlnghhfgrtnnlgedjlftrbdeut
|
- OATH-HOTP and OATH-TOTP are 6-8 digit one-time passwords that change within 30 seconds. In TOTP codes, the code is generated using a hash HMAC(sharedSecret, timestamp), where the timestamp changes every 30 seconds. The shared secret is often provided as a QR code or pre-programmed into a hardware token. And HOTP codes use an authentication counter instead of a time stamp. So when setting up this feature, it’s important to make sure the timer on the device is set to the correct time.
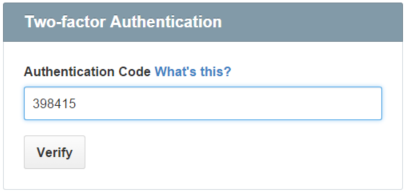
-
Benefits of using OTP on YubiKey
- Secrets always remain on YubiKeys. It is impossible to read information from them. And from the phone or computer, in case of hacking and launching of spy software, information can be read.
- The keys do not require recharging, unlike the phone, which is very often used for two-factor authentication. So even if you forget to recharge, you can access your accounts anywhere using hardware devices.
OTRs caused by touch on the computer
If you configure the OTP password function on the YubiKey so that it is triggered by touch, the authorization process will look like this:
- at the request of the server, you need to insert the key into the USB socket;
- place the mouse cursor in the text field;
- touch the golden metal part and the key will automatically transmit the OTP password.
OTRs caused by touch on a mobile device
Since the mobile device has an NFC function, the authentication process is a little different – you need to bring the key to the back of the phone, touch the screen where the password should be entered. Also, the key can be connected to a mobile device using the appropriate interface: USB-C or Lightning.
How to configure OATH-HOTP and OATH-TOTP
You can configure the one-time password function on the YubiKey in two ways:
- set to call by touching OTP-passwords using the YubiKey Manager (recommended) or CLI tools (for this, appropriate developer experience is required);
- using the Yubico authenticator app (instructions).
Thanks to an intuitive interface, you can quickly configure the relevant features and use the hardware devices to their fullest extent to increase the security of your accounts and protect against phishing.
If you don’t know which YubiKey will best suit your needs, we recommend taking a quick test.
Similar materials in the Knowledge Base
How to set up a YubiKey in Linux using call-response
YubiKey hardware security keys make your system more secure. And the procedure of logging into accounts is faster and more convenient. Follow the instructions below to easily add the required settings on your Linux system.Setting up the YubiKey in Linux is quite...
5 ways to install Yubico software on Linux
To use YubiKeys on a Linux system, you will need to install the appropriate Yubico software: Yubico authenticator; YubiKey Manager; Built-in repositories; Yubico PPA packages; Compilation from the source code. Installing the Yubico Authenticator There are several ways...
How to configure YubiKey on Linux using U2F function
With the help of YubiKey hardware security keys, your system receives an increased level of protection, and the process of logging into accounts becomes faster and more convenient. To easily configure the necessary parameters on a Linux system, you should follow the...