Binance is one of the largest and most popular cryptocurrency exchanges in the world. With its help, you can monitor the movements of the cryptocurrency market, invest in digital assets and conduct trading operations in real time.
Of course, in order to use the platform effectively, you must first protect your accounts and wallets from potential attackers. Because the more popular the industry becomes, the more cryptocurrency fraudsters appear, who constantly develop new ways to deceive users of the exchange.
How attackers can gain access to wallets
Common methods of attackers’ attacks are:
- Impersonating Binance employees.
- Sending fake messages from law enforcement agencies.
- Phishing attacks.
You should always be on the alert and be wary of any unusual messages that you did not expect to receive.
How to recognize intruders who pretend to be employees
The first thing to remember is that employees of any company will never ask for personal information or try to contact you through unofficial channels. To communicate with Binance staff provided chat. Even if communication through messengers or mail is intended, you will be warned about it through official messages in your account. In any case, upon receiving a suspicious message, it is better to immediately write to the company’s support by logging in to the Binance website.
How to recognize fake messages from “law enforcement officers”
Usually, fraudsters pretending to be law enforcement officers try to get you to do something quickly and without thinking by threatening to block your account. For example, they may say that funds came into your account from suspicious sources, so a money laundering investigation has begun. Then, under this pretext, they can request your confidential data, or ask to transfer some amount of funds to supposedly confirm your identity or hide all the money “in a more reliable wallet”.
In fact, law enforcement officials will not contact you by mail or call you about this, nor will they ask for passwords or PINs. Do not respond to such messages, rather check the official messages from the company immediately or contact Binance support to make sure that your wallets have not been seized.
What are phishing attacks and how to protect against them
Phishing attacks or phishing are one of the means of influence by attackers using social engineering. The main goal of scammers is to obtain sensitive information: full username, password, two-factor authentication code, PIN, etc. In order to obtain this data, an attacker can impersonate another person or send fake – fake official – forms to fill out and malware.
Examples of phishing attacks:
- application from an address that is similar to the address of the official website (may differ by 1 or more characters);
- a link to a fake site (the address of which may also be slightly different);
- an application from a fake account of a company employee in social networks;
- malicious programs offered to be downloaded by an alleged employee of the company under the pretext of a software update or a law enforcement officer in order to “verify the account”;
- hidden buttons in browsers that help attackers get data when the user touches them;
- exploiting the vulnerabilities of unprotected free Wi-Fi networks.
Since the most vulnerable link during phishing attacks is a person, the main protection against attackers is constant vigilance.
How to understand that you are being attacked:
- Very often, messages from criminals have typographical and lexical errors, and errors can also be located in the domain of the site.
- Usually, fraudsters try to create a sense of urgency, for example, for a person to transfer funds to “safe accounts” before the wallets are blocked.
How to protect yourself from phishing attacks:
- Pay attention to errors, check the correct spelling of the site address. Valid addresses only with domains binance.com and binance.net.
- It is better to find the site through the search (once again checking the correctness of the domain), or go to it through the bookmarks created earlier in the browser.
- Check the https certificate (open the lock next to the site address) to ensure that the domain name is genuine.
- Update your browsers regularly. But do not ignore the warnings about switching to a dangerous site, which usually appear in Google Chrome and Mozilla Firefox.
- Enable two-factor authentication and never share your code with other people.
And the main thing — add a YubiKey security key as an additional means of protecting your account. Attackers will not be able to bypass this protection, even if they get your passwords. Because YubiKey hardware security keys work according to the principle of an apartment or car key: if you don’t have the key, you can’t get inside.
How to Add YubiKey Security Key to Binance
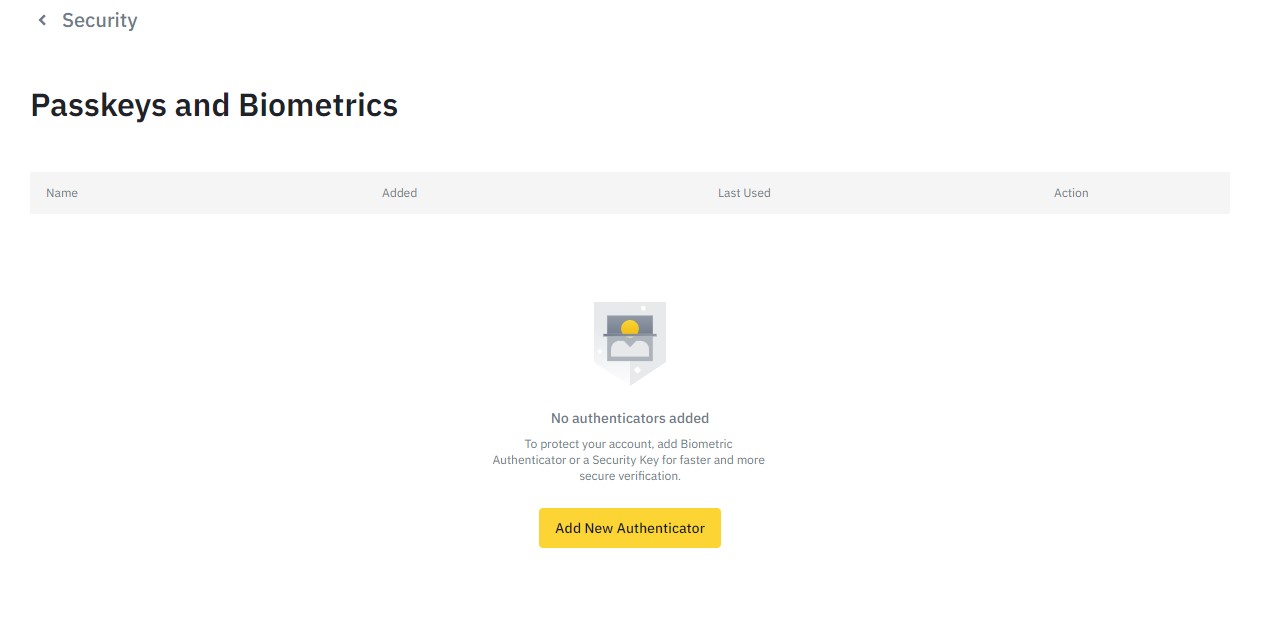
Buy the YubiKey security key from the official website in Ukraine. If you already have the key, log in to your account on the site and open the “Profile” tab. Find the “Access keys and biometrics” item.
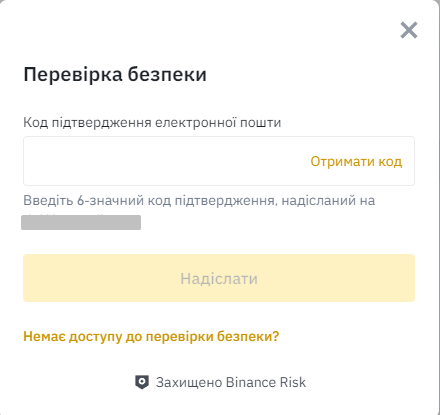
Click the “Add new authenticator” button and enter the code that will be sent to your e-mail upon your request.
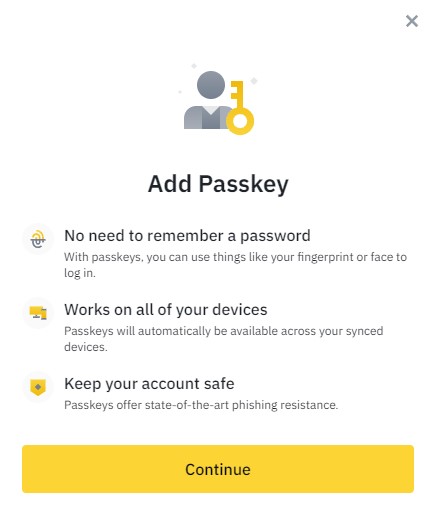
After that, the program will prompt you to add a key.
Next, depending on your operating system, you will receive a message about adding a key. The system may prompt you to insert or hold the key to the device, enter a PIN, touch the key, etc.
After fulfilling all the requirements, you will receive a message that the verification was successful.
In your profile you will see all your added hardware devices.

After that, a key will be required for any action in the profile — changing email or phone, confirming transactions. In this way, your account will be reliably protected from phishing. We always recommend adding a spare key to your account in case one of the keys is accidentally lost. To do this, you will need to go through all the steps above.
The good news is that any YubiKey security keys available in our online store are compatible with the Binance cryptocurrency exchange. And the spare key does not necessarily have to have the same form factor as the main one. So by purchasing an additional key, you close the need to protect accounts in various services.
If you don’t have a key yet, or you want to buy a spare, go to our online store right now!
Similar materials in the Knowledge Base
YubiKey Smart Card Mode on macOS – convenient authentication for developers
Smart cards have been very popular for many years as a reliable means of identification, authentication, and authorization in businesses and educational institutions. They come in a variety of form factors: from a SIM card on a phone to a plastic card. However, if you...
OTP passwords on YubiKey — how it works
OTP passwords are one-time passwords (the origin of OTP is from English one time password) that are used for one authentication session. Their effect is usually limited by time. You may have received such codes by phone or mail when trying to access online banking or...
Yubico Authenticator – User Guide
This guide is designed to help you set up your YubiKeys on any services that offer two-factor authentication connections using authenticator programs that generate codes.




