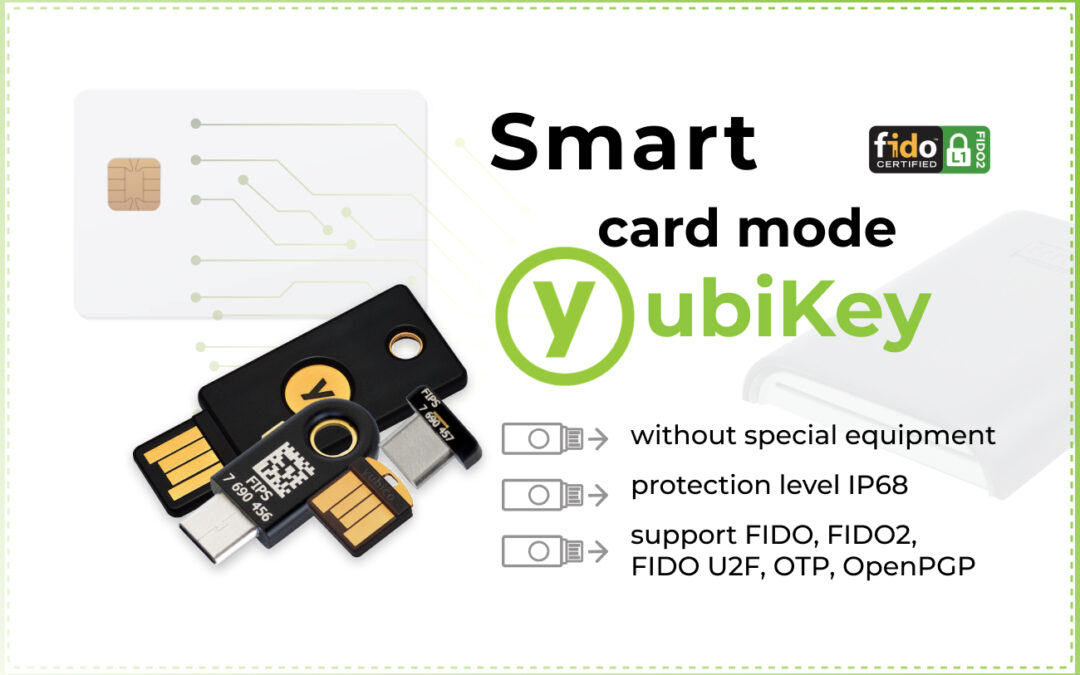
Yubikey smart card mode without additional equipment
The idea of the first smart card was patented by the French inventor Roland Moreno back in 1974. Today, we already use this technology every day and cannot imagine how we can do without it: SIM cards, electronic travel tickets and passports, keys to hotel rooms, employee passes of closed enterprises, and bank payment cards work in smart card mode.
In business, smart cards are indispensable assistants, especially if you need to protect the IT infrastructure from hacking and phishing. But reading such cards usually requires additional equipment that can read the information. And the service life of plastic smart cards is mostly 2-3 years, which means that information security costs are increasing. What to do now?
There is a rather sophisticated solution to this issue: some series of YubiKey security keys (US development) can not only open access to personal or corporate accounts, but also work in smart card mode. In addition, they will last at least three times longer thanks to their shock resistance, water resistance and no removable/retractable parts.
Let’s consider the features of smart cards and the effectiveness of replacing them with YubiKey security keys.
What are smart cards?
Smart cards are small devices with an embedded microcircuit, sometimes a microprocessor, and an operating system that allow them to generate keys, store identifying information about the owner, and perform cryptographic calculations.
They most often look like plastic cards and work only in connection with reading equipment – a terminal that transmits data to a computer.

But, as we mentioned above, there are exceptions. Some manufacturers produce hardware devices that are similar in function and properties to smart cards, and they already include a card reader function. These are tokens or security keys with a USB interface, such as the YubiKey. The latter are considered one of the best in terms of price-quality ratio.
Smart cards are used to establish the authenticity of the identity of their owners (identification and authentication), as they are reliably protected from unauthorized access thanks to embedded software. The data contained on them cannot be copied, and the devices themselves cannot be reprogrammed. It is not for nothing that smart cards are used by various financial and government structures, restaurant/hotel businesses, scientific/educational centers and large IT companies.
The main functions of a smart card:
- storage of identification data of the owner (for example, ID);
- authentication based on the “challenge-response” principle (a method in which the secret or password is not transmitted over the communication channel);
- storage and verification of PIN codes for two-factor/multi-factor authentication;
- generation and storage of digital signature, keys, or certificates.
An example of solving these problems is the SIM cards of mobile operators – with their help, it is possible to prove that the subscriber who connected to the network by a certain number is really a client of the operator and services are available to him within the framework of his tariff.
Note. YubiKey’s security keys have all the listed functions. In addition, their use does not require additional equipment, such as readers or card readers, since the keys can be directly connected to computers.
Types of smart cards
Smart cards differ in functionality:
- memory cards (as cards for micropayments in transport);
- smart cards (like biometric passports, SIM cards).
Also, smart cards differ in the way they interact with other devices:
- contact, with the ISO 7816 standard (the basic standard for all smart cards, which is most often used in bank cards);
- contact, with a USB connector (these include not only ISO 7816 cards with built-in USB, but also tokens, security keys);
- contactless (such cards have radio frequency readers/transmitters or so-called RFID tags — RFID identifiers).



Note. YubiKey keys belong to intelligent types of equipment and can be connected via USB or contactless, transmitting data via NFC.
Smart card mode in YubiKey
YubiKey’s security keys support the following protocols:
- PIV (personal identity verification) smart card — confirmation of identity;
- smart card CCID (integrated circuit card interface device) is an interface device with an integrated circuit that allows connection via USB and does not require readers.
This allows you to use the following functions:
- key management;
- signature of documents;
- encryption of mail messages;
- connection of two-factor authentication (ownership factor — card, knowledge factor — PIN code);
- enable passwordless authentication.
Also, some series of YubiKey keys support NFC technology, which allows you to connect to devices contactless. In particular, these are the following series:
- YubiKey 5 NFC;
- YubiKey 5C NFC;
- Security Key NFC;
- Security Key C NFC;
- YubiKey 5 NFC FIPS;
- YubiKey 5C NFC FIPS.
Below are their photos and links, where you can familiarize yourself with the characteristics of the devices in more detail.
Note. The YubiKey FIPS series keys are similar in appearance to the YubiKey 5 series keys, but with enhanced protection – designed specifically for government officials and enterprise employees, these keys are provided only by individual order.
YubiKey series with smart card mode
Smart card mode is supported in YubiKey series:
- YubiKey 5;
- YubiKey 5 FIPS.
Each of them has 6 types of keys that differ in form factors.
YubiKey 5
The keys of this series support not only smart card mode, but also FIDO2, U2F, OTP, OpenPGP 3 protocols. The keys are also crush-resistant and waterproof, meeting the degree of protection IP68.
This YubiKey series features the following products:
- YubiKey 5 NFC is a hardware key with a USB-A connector and NFC wireless technology;
- YubiKey 5C NFC is a hardware key with a USB-C connector and NFC wireless technology;
- YubiKey 5C is a hardware key with a USB-C connector;
- YubiKey 5Ci is a hardware key with a USB-C and Lightning connector;
- YubiKey 5 Nano is a miniature device with a body that protrudes minimally from the PC and a USB-A connector;
- YubiKey 5C Nano is a miniature device with a minimally protruding body and a USB-C connector.
YubiKey 5 keys can be purchased by both business and average users who are concerned about network security, online payments, have savings on cryptocurrency exchanges or are a freelancer/remote employee.
YubiKey 5 FIPS
As we mentioned above, the keys of this series are a separate development that is ideal for employees of large businesses, banking, or government agencies. They are the ones that support the PIV (identity verification) smart card mode, and also have the ability to:
- key management;
- connection of one-/two-/multi-factor authentication (support of FIDO, FIDO2, FIDO U2F protocols);
- generation of OTP passwords taking into account the time factor or counter;
- save up to 32 accounts.
In addition, YubiKey FIPS keys can be numbered to enable tracking of employee locations across the enterprise or active employee sessions on personal computers by ID. In the event that an employee resigns, it is possible to reprogram the keys for reassignment to another person.
The YubiKey FIPS series includes the following products:
- YubiKey 5 NFC FIPS – security key with USB-A interface and NFC wireless communication technology;
- YubiKey 5C NFC FIPS – security key with USB-C interface and NFC wireless communication technology;
- YubiKey 5C FIPS – security key with USB-C interface;
- YubiKey 5Ci FIPS – key with USB-C and Lightning interface;
- YubiKey 5 Nano FIPS is a miniature device with a minimally projecting body and USB-A interface;
- YubiKey 5C Nano FIPS is a miniature device with a minimally projecting body and USB-C interface.
Note. Please note that YubiKey FIPS series keys are provided only by individual order.
Where to get YubiKeys with smart card function
YubiKey’s security keys are produced in the USA together with Sweden. We, The Kernel, are the official distributor of Yubico in Ukraine and offer our customers original products.
You can order products from us in bulk by contacting the manager by phone +38 (044) 35 31 999, or in retail — on the official website our online store.
Need help with product selection or advice on specific safety preferences? Contact us. We have been working in the field of information security for more than 30 years, therefore, in addition to ordering YubiKey products, we can offer recommendations for solving any issues related to the protection of your IT infrastructure.